Fortinet FortiClient VPN/ZTNA
Zero Trust Security

The ZTNA Edition of FortiClient provides the requirements for a remote worker to connect to the network with a minimum level of control. This edition enables both ZTNA and VPN encrypted tunnels, as well as URL filtering and USB device control. Central management via FortiClient EMS is included.
| Features include: | |
|---|---|
| Zero Trust Agent with Multi-factor Authentication (MFA) | The Zero Trust Agent supports ZTNA tunnels, single sign-on (SSO), and device posture check to FortiOS access proxy |
| Central Management via EMS or FortiClient Cloud | Centralized FortiClient deployment and provisioning that allows administrators to remotely deploy endpoint software and perform controlled upgrades. Makes deploying FortiClient configuration to thousands of clients an effortless task with the click of a button. Vulnerability dashboard helps manage an organization’s attack surface. All vulnerable endpoints are easily identified for administrative action. Windows AD integration helps sync an organization’s AD structure into EMS so the same organization units (OUs) can be used for endpoint management. Realtime Endpoint Status always provides current information on endpoint activity and security events. |
| Central Logging and Reporting | Centralized logging simplifies compliance reporting and security analysis by ForiSIEM or other SIEM product |
| Dynamic Security Fabric Connector | EMS creates virtual groups based on endpoint security posture. These virtual groups are then retrieved by FortiGate and used in firewall policy for dynamic access control. Dynamic groups help automate and simplify compliance for security policies. |
| Vulnerability Agent and Remediation | Vulnerability agent and remediation ensures endpoint hygiene and hardens endpoints to reduce the attack surface. This identifies vulnerable endpoints and prioritizes unpatched OS and software vulnerabilities with flexible patching options including auto-patching. |
| SSL VPN with MFA | Secure Socket Layer (SSL) Virtual Private Network (VPN) with MFA enables an easy-to-use encrypted tunnel that will traverse most any infrastructure. |
| IPsec VPN with MFA | IP Secure (IPSec) VPN with MFA enables an easy-to-use encrypted tunnel that provides the highest VPN throughput. |
| FortiGuard Web Filtering | Powered by FortiGuard Labs research, the web filtering function monitors all web browser activities to enforce web security and acceptable usage policy with 75+ categories. It works across all supported operating systems and works with Google SafeSearch. The endpoint web filtering profile can be synchronized from FortiGate for consistent policy enforcement. Administrators can set black/white lists, on-/off-net policies, and import FortiGate web filtering policies for consistent enforcement. FortiClient now supports a web filter plugin that improves detection and enforcement of web filter rules on HTTPS sites with encrypted traffic. |
| Split-tunneling | Supported on ZTNA and VPN tunnels, split-tunneling enables optimized user experience. |
| Single Sign-on (SSO) | SSO integrates with FortiAuthenticator identity and access management to provide single sign-on. |
Learn More:
Overview:
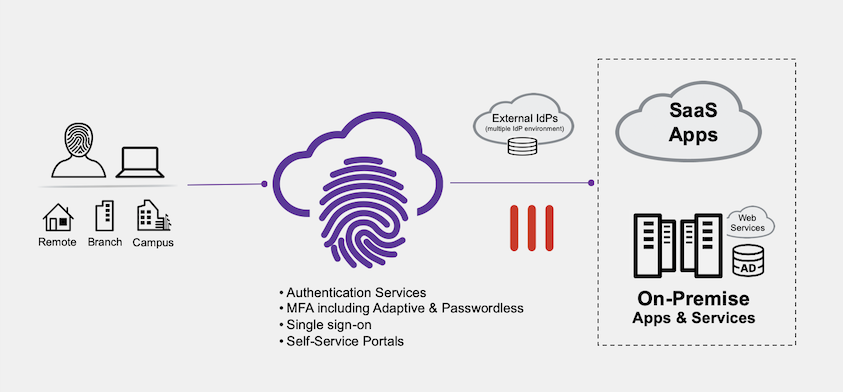
forti fied access is cloud-based and natively integrated with the Fortinet Security Fabric to deliver a rich set of security controls and centralized management of user authentications, including multi-factor authentication. FTI enables you to begin your zero-trust journey with reliable user verification and strong authentication, plus ease-of-use for the end user. Adaptive, multi-factor, or passwordless authentication and identity federation for SSO across the enterprise hybrid environment are all included via user-based licensing.
Identity and Access Management Solution
Concerns about security, end-user experience, and the overall cost of a unified IAM (Identity and Access Management) solution are rising as enterprises embrace digital business initiatives—including work-from-anywhere for their workforce. FortiTrust Identity is a cloud-delivered IAM solution that uses modern authentication technologies while leveraging existing network infrastructure to enable organizations to secure user access to cloud and on-premises applications and services.
Pricing Notes:
- Pricing and product availability subject to change without notice.
Features & Benefits:
Ensure the right people get appropriate access to your data, resources, and applications across the enterprise
Identity and Multifactor Authentication Management
Increase certainty of user identity with the verification of another factor and adaptive authentication technique
Single Sign-on (SSO) for Cloud Applications and On-Prem Services
Fortinet SSO including modern authentication protocols federating identity for SSO (SAML, oAuth/OIDC, and API support)
Guest, BYOD, and Certificate Management
Customizable portals including self-service capabilities
Simplify Deployment and Identity Access Management
Natively integrated with Fortinet Security Fabric, no additional onsite hardware, software or ACL changes required for hybrid IT environment
Integration with Secure Directories, and Interoperable with External Cloud Identity Proiders (IDPS)
Leverage existing identity systems of record on-premises or in the cloud.
Pricing Notes:
- Pricing and product availability subject to change without notice.
Capabilities:
Highly Available Identity-as-a-Service
- Hosted in Fortinet Data Center
- 24/7 Monitoring
Authentication Service
The authentication service built into FortiTrust Identity provides authentication for employees, partners, and contractors via our access identification and verification methods, including our IdP broker/proxy capability that works seamlessly with external IdPs. With FortiTrust Identity, organizations can consolidate several methods into one experience with a single view of managing identity. FortiTrust Identity supports industry authentication and authorization standards:
- Cloud/web types: SAML, OAuth2, and OIDC
- MFA or strong authentication: OTP, email, SMS (OTP), and FIDO2 security with a variety of hardware form factors and mobile apps. Organizations can choose a factor (or factors) that best fits their environment. Specifically, organizations can secure cross-platform token transfer with the mobile apps for their iOS and Android devices
- Adaptive authentication uses the information gathered at a login attempt to evaluate the circumstantial risks of a given login attempt. This information includes time of day, geo-location, historical usage pattern, etc. The second authentication factor is only requested when that risk is higher than a predetermined threshold. Furthermore, the login attempt can be blocked if the circumstantial risk is high enough
SSO
- SSO simplifies the end-user experience and reduces the need for repeated authentications to gain secure access across enterprise applications and services
Interoperability
- FortiTrust Identity provides IdP broker/proxy capability outof-the-box for organizations that have identities managed across multiple external IdPs. This provides a centralized authentication service across these external IdPs, enabling organizations to have a uniform policy and MFA method independent from external IdPs
Integration
- Integration natively with Fortinet Security Fabric, specifically with FortiGate, extends authentication services for secure user access to on-premises resources. No additional gateway or software agents are required to purchase, install, and maintain
Certificate Management
- Streamlined certificate management enables rapid, costeffective deployment of certificates
Pricing Notes:
- Pricing and product availability subject to change without notice.
Specifications:
| Identity | |
|---|---|
| Highly Available Secure Managed Service |
|
| FortiToken Mobile Push |
|
| MFA Service Integrated with FortiGate and Other Fortinet Products |
|
| FortiToken Mobile Token Codes |
|
Pricing Notes:
- Pricing and product availability subject to change without notice.
Documentation:
Download the Fortinet FortiTrust Identity Datasheet (PDF).
Download the Ordering Guide (.pdf).
Pricing Notes:
- Pricing and product availability subject to change without notice.